How long can we continue to rely on hardware/critical electronic devices without being able to properly assess their security?
There is a gap between the threat and the operational response capacity of the actors in the fields of IoT, Hardware and embedded Software. Therefore the risks of attacks increase on the processed data in the world of Internet of things (private data, sensitive device supervision, industrial process, HealthCare products, etc.).
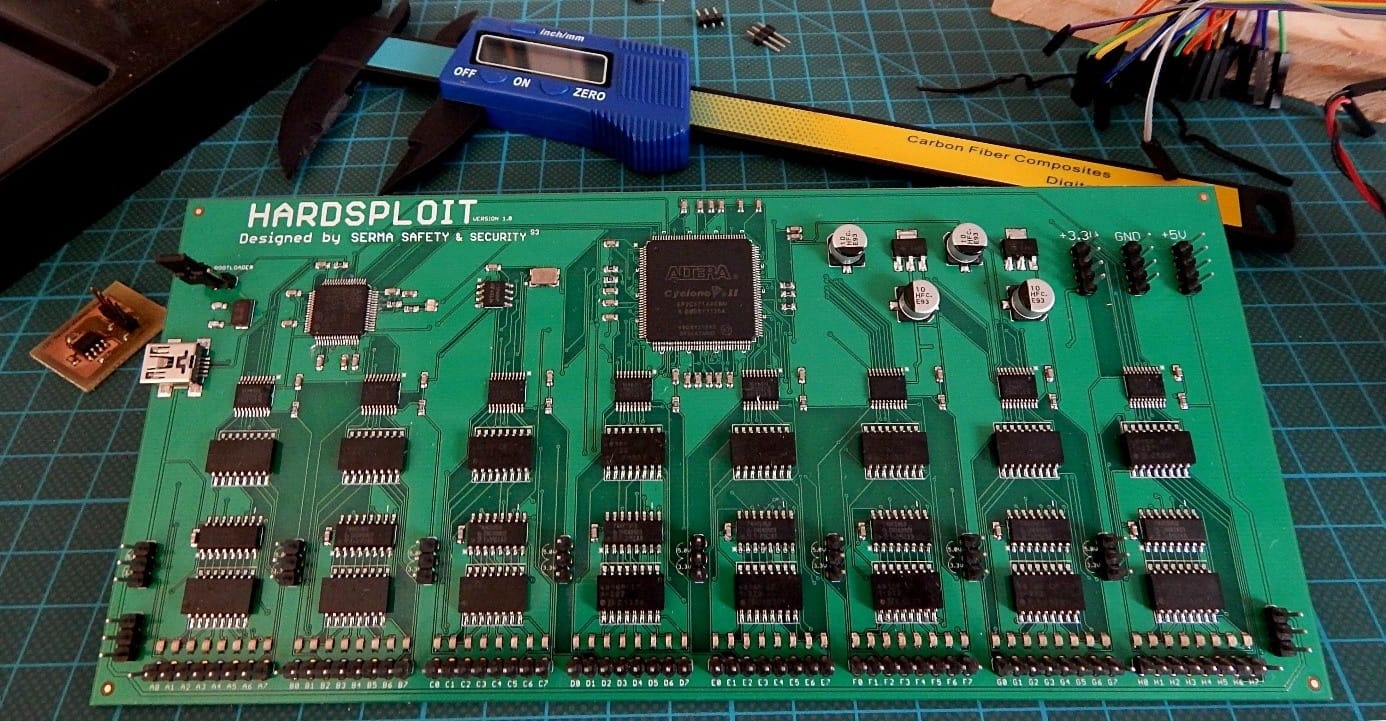
Hardsploit is a tool with software and electronic audit features based on a modular and programmable platform (FPGA component). It can be used to perform security tests on electronic communications interfaces for embedded devices. It’s actually a complete Framework!
Hardsploit Modules will let Hardware testers intercept, replay and/or and send data through each type of electronic bus used by the Hardware Target. The Level of interaction that testers gain thanks to Hardsploit depends on the electronic bus features: JTAG, SPI, I2C’s, parallel address & data bus on chip, etc.
Hardsploit is developped as an R&D project from the Security Consulting team in SERMA. In 2015, the tool was launched from the observation that there was no automated search tool for vulnerabilities in the field of embedded electronics. The team continues developing and maintaining the Software, while a local French company manufactures the Hardware based in Rennes (France).
While continuing the innovations of HardSploit V1, which allows attacking only one interface at a time, the SERMA teams are working on a second innovative version: HardSploit V2.
The delivery of HardSploit V2, which will enable multi-interface audits at the same time, is planned for 2020.
Also, an evolution integrating the power of the artificial intelligence through the identification by neural networks of the electronic communication BUS is planned for 2021.
With these developments, SERMA aims to:
- detect the interfaces or BUS of electronic communication,
- identify the components or communication protocols with AI,
- communicate with the detected BUSs,
- Find and exploit vulnerabilities.
Hardsploit is known around the world as a hardware intrusion test tool and is used in training for manufacturers and hardware auditors.
HardSploit allows the user to attack/audit the debug ports and component communication ports with a simple interface.
Debugging ports (JTAG and SWD) and administration interfaces (UART) are normally used by manufacturers to program and test components. Nevertheless, an auditor, much like a malicious person, will be able – with HardSploit – to divert the function for these interfaces in order to recover the softwares (called Firmware in the case of the microcontrollers) and cryptographique keys.
This is also true for the communication interfaces of the electronic components: the I2C, SPI or CAN. These interfaces can be used to store data, often sensitive and mostly unencrypted, on external memories. Several components can be found on these communication lines (called communication BUS) such as on-board sensors or wireless systems (Bluetooth, Wifi, Ethernet, etc.). By connecting intercepting these BUSs, the listener can capture sensitive information or inject malicious data with HardSploit.
References:
- Chaos Computer Club in Germany : https://www.youtube.com/watch?v=5xCx9C5vyKM
- Hack in Paris : https://www.youtube.com/watch?v=foeCXe_Gzhc
- BlackHat in Las Vegas: https://www.blackhat.com/us-16/training/hardware-hacking-with-hardsploit-framework.html
For more information, please visit: https://twitter.com/HardSploit