Blog Post 1
In the Beginning, a Simple Ambition: Democratizing Hardware Cybersecurity
Nearly 10 years ago, in 2015, a small team of cybersecurity enthusiasts embarked on an entrepreneurial adventure within a modest company from Brittany called Opale Security. At a time when Bitcoin was worth just $500, 3D printers struggled to spit out plastic spaghetti rather than finished objects, and everyone was still wondering what drones would actually be useful for, these passionate tinkerers dove into all sorts of experiments. They installed AntMiners, developed their own electronic boards using pick & place machines and hydrochloric acid PCB etching, and assessed the security of early drones controlled with hacked Wii remotes. But behind all of this lay one consistent goal: understanding how things worked, and what was at stake in terms of cybersecurity.
These brilliant makers had an ambitious objective: to make cybersecurity accessible to all. As electronics enthusiasts concerned by the generally low level of hardware security awareness, they came up with the idea of creating a tool that could democratize cybersecurity testing in this domain.
And One Day, the Idea Took Shape
Sharing their vision and ambitions at numerous conferences, including Black Hat 2015, the concept found its audience. Encouraged by these early positive feedbacks and supported financially by the Brittany region, the team decided to embark on the somewhat crazy project of creating a board that would bridge the IT world and hardware, inviting digital security specialists to also focus on electronics security. The goal was to ease the transition from a universe governed by bits and bytes to one ruled by volts and amperes.
The motto was clear: design an intuitive interface paired with an easy-to-use board. Driven by the joy of creation and their thirst for discovery, they kicked off the project using the most current and innovative technologies and programming languages, while aiming to develop a tool that would be both fast and efficient. This is how the first version of Hardsploit was born.
A Symbolic Name Choice
As you might have guessed, the name Hardsploit wasn’t chosen by chance. It’s primarily a blend of HARDware and exPLOITation. “Hardware” highlights the attack surface represented by the electronics that make up the board or system under study, while “exploit” clearly signals that the goal is to go all the way to exploiting identified vulnerabilities.
And for those who might have missed it, the name is also a tribute to the tool Metasploit, which shaped the early days of many pentesters and was originally designed for network and software penetration testing.
Thus, Hardsploit was meant to be a logical name illustrating the ambition to help the community more easily identify hardware vulnerabilities and assess the impact of their exploitation.
And SERMA Completed the Journey with Version 1.0
It was at this point that the small company was acquired by SERMA Safety & Security, affectionately known as S3 (pronounced “S Cube”), the cybersecurity subsidiary of a group specializing in testing and services for the electronics industry. Version 1 was thus launched under the SERMA Safety & Security brand. Although this first version was not without its flaws, it laid the foundation for a tool capable of helping both beginners and experienced specialists perform hardware security tests in the simplest and most effective way possible.
This first version consisted of several components:
A graphical interface developed in Ruby and QT (a real trend at the time),
Embedded code in C language for the microcontroller,
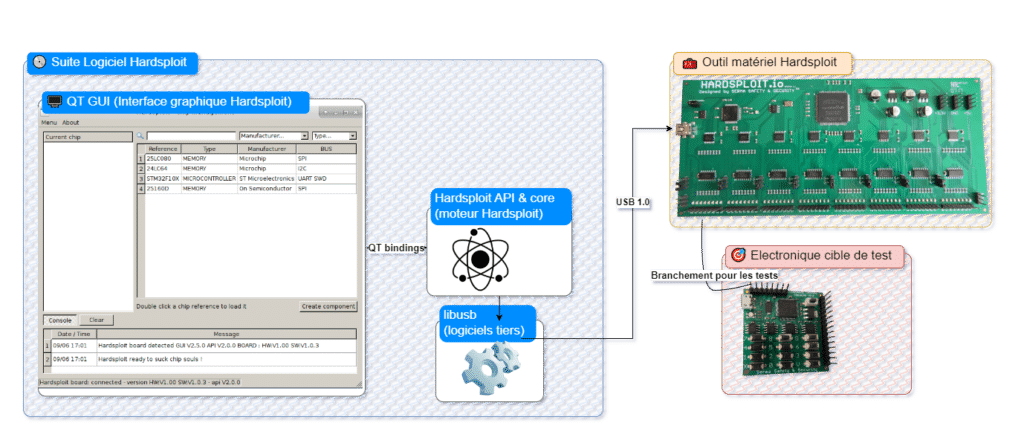
This architecture allowed the user to visualize in real time the inputs and outputs of the targeted component, and even to see exactly where on the board to connect their wires before soldering them onto the target. Having personally conducted several trainings using this version of Hardsploit, I saw more than one participant’s eyes light up when discovering this feature. Spoiler alert: we will probably keep it for the new version…
Although the tool wasn’t perfect, as I mentioned earlier, innovation was definitely there. Of course, some limitations quickly became apparent. For example, despite a polished graphical interface, users still needed to master some fundamentals, like knowing where to connect and what to look for. Ideally, when a tool is intuitive enough, there shouldn’t be a need for specific training on either the tool itself or hardware attacks; at most, a quick start tutorial would suffice. Easier said than done when it comes to electronic penetration testing. That’s why we will revisit the key stages of a hardware audit in future blog posts.
Once finalized, the project allowed us at S3 to develop specialized training on electronics and embedded security, based on an ideal educational tool. And here, considering customer feedback, we can regard Hardsploit as a success.
However, it must be admitted that, looking at the product itself, its early flaws and the positioning we hadn’t sufficiently studied meant we didn’t achieve the expected success. Amid the fast pace of S3’s development, the project was put on standby.
The World Has Changed, and Hardsploit Needed to Be Reborn
Over the past ten years, however, the technological landscape has evolved dramatically, and connected devices are now everywhere. I’ve experienced this firsthand at home: having recently bought a mid-range oven, I was surprised to discover it came equipped with a Wi-Fi module, offering remote control of my cooking, a feature I must admit I’ve never actually used since the oven was installed. Whether it’s watches, lighting, electrical grids, cars, buildings, or heating systems, just take a look around to realize that almost everything these days is connected. Often, these devices sync to the “cloud”, that is, one or multiple servers owned by third parties that aren’t always clearly identified or identifiable.
Even the industrial sector hasn’t escaped this revolution. Industrial networks, now prime targets for attackers, require continuous updates. Yet these networks often exist in isolated environments, necessitating specific solutions to stay connected and secure.
It is within this all-connected context, with a multiplication of technologies and protocols, and a widespread negligence by many manufacturers regarding cybersecurity, that regulators, both governments and private market regulators, are increasingly pushing for standards and regulations. These force manufacturers and solution providers to manage their cybersecurity, assess their risks, handle vulnerabilities, and test their products…
This combination of technological frenzy and the need to control inherent cyber risks convinced us that it was the right time to bring back our trusty old Hardsploit and evolve it to meet the growing community demand for security testing. Although improvements had already been planned as early as 2016, the context and available technologies at the time weren’t favorable to such an idea.
Whats next ?
Today, we are convinced that by evolving the proof of concept developed in 2015 to meet current challenges, we can offer the cybersecurity community a mature enough tool to help meet regulatory requirements and significantly improve the cybersecurity level of electronic products. The vision is for a multi-sector tool that is intuitive, ergonomic, and accessible even to beginners, enabling us to regain control in the ongoing cat-and-mouse game that is cybersecurity.
That’s why, starting in 2020, leveraging my experience with the first version and feedback from field missions at S3, I worked with our teams and those of the SERMA group to relaunch a project aimed at developing a new version of Hardsploit. We kept the original spirit: if we want tomorrow’s products to be more secure, we must make security more affordable and accessible by using the most current and innovative technologies available.
And today, thanks also to support from BPI through the France 2030 funding program under the Critical Technologies 3 call for projects, we are launching in 2025 the design of this new tool, which we have “modestly” named HardsploitNG (Hardsploit Next Generation).
In upcoming posts on this blog, I invite you to discover in greater detail the new features and specifics of this next-generation tool.




