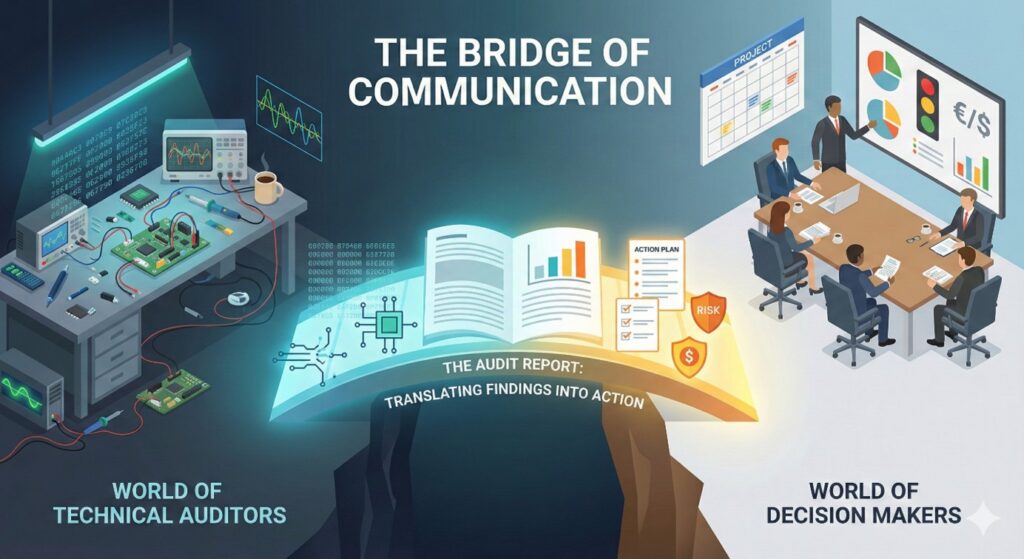
Cyber risk analysis has become a fundamental component of securing any modern organization. In a world where digital threats are constantly evolving, the ability to understand and anticipate these threats is essential for protecting our assets, our reputation, and our business continuity.
This article explores the fundamentals of cyber risk analysis and highlights its growing importance in today’s context.
What Is Cyber Risk Analysis?
Cyber risk analysis is a structured process used to identify, assess, and prioritize potential threats to an organization’s information systems.
Its main objective is to understand existing vulnerabilities and estimate the potential impact of a cyberattack.
Main Objectives
- Identify critical assets (sensitive data, infrastructure, software) and potential threats (cyberattacks, human error, technical failures).
- Assess technical vulnerabilities (outdated software, weak configurations) and organizational weaknesses (lack of training, missing procedures).
- Analyze the impact and likelihood of risks, taking into account potential financial, operational, and reputational consequences.
Key Steps in Cyber Risk Analysis
- Asset Identification: Inventory all critical systems, data, and resources within the organization.
- Threat Evaluation: Analyze possible types of attacks and identify potential malicious actors.
- Vulnerability Assessment: Examine weaknesses in current systems and processes.
- Impact Estimation: Evaluate the possible consequences of a successful attack.
- Risk Prioritization: Rank the identified risks based on their severity and likelihood.
Tools and Methodologies
Several standardized methodologies exist to conduct cyber risk analysis, including EBIOS RM, ISO 27005, and NIST SP 800-30.
These frameworks offer structured approaches to consistently evaluate and manage risks.
Why Cyber Risk Analysis Matters
A well-executed cyber risk analysis allows organizations to:
- Allocate security resources efficiently
- Justify cybersecurity investments
- Improve resilience to evolving threats
- Comply with current regulations (GDPR, NIS2, etc.)
Cyber risk analysis is not a one-time task but a continuous process that must evolve alongside the threat landscape.
By embedding this practice into our corporate culture, we strengthen our ability to protect digital assets and maintain stakeholder trust.
Every employee plays a role in this effort—by staying alert and reporting any suspicious activity, they contribute to the collective security of the organization.