Blog Post 2 #1
Diving into the world of hardware penetration testing
Imagine this: you’re holding a brand-new connected device, ready to join the growing family of your smart gadgets. Behind its sleek design lie circuits, chips, and interfaces, and sometimes, a few hidden security vulnerabilities. This is where hardware penetration testing comes in, also known as Cybersecurity auditing, or simply pentest. This audit process involves thoroughly examining the resilience of an electronic device against malicious attacks by hackers. But make no mistake: it’s far from a simple treasure hunt. It’s a true obstacle course, where every step demands method, curiosity, and, above all, the right tools.
A five-act play
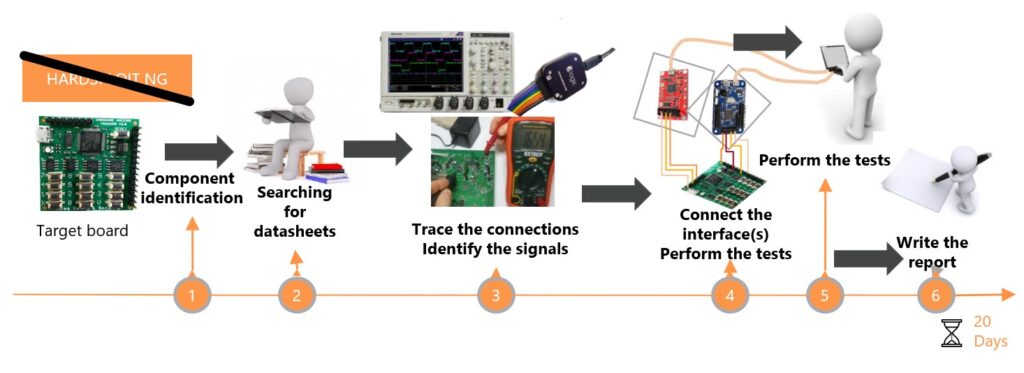
Hardware pentesting is a bit like a detective story told in multiple chapters. It starts with reconnaissance, gathering all publicly available information about the device. Then comes the hands-on phase: disassembling the device to explore its inner workings and understand how it functions. Documentation, observation, identification of components and interfaces, it’s all part of this methodical exploration phase, where every detail matters for the rest of the investigation.
Once the circuit board is mapped out, it’s time for analysis. This means diving into the internal operation of the device: studying its interfaces and communication protocols, identifying the attack surface, with the ultimate goal of taking control of the device or extracting its firmware to reverse engineer the code. This is the stage where we try to piece everything together, and most importantly, find where potential vulnerabilities might be hiding. It requires precision, a solid set of hardware and software tools, and a good amount of patience and perseverance.
If vulnerabilities are discovered, the exploitation phase begins. This is when we test potential attack scenarios in practice: reading or modifying memory, manipulating interfaces, injecting commands, and so on. The aim is to verify the real impact of the vulnerabilities identified, and to demonstrate how far an attacker could go.
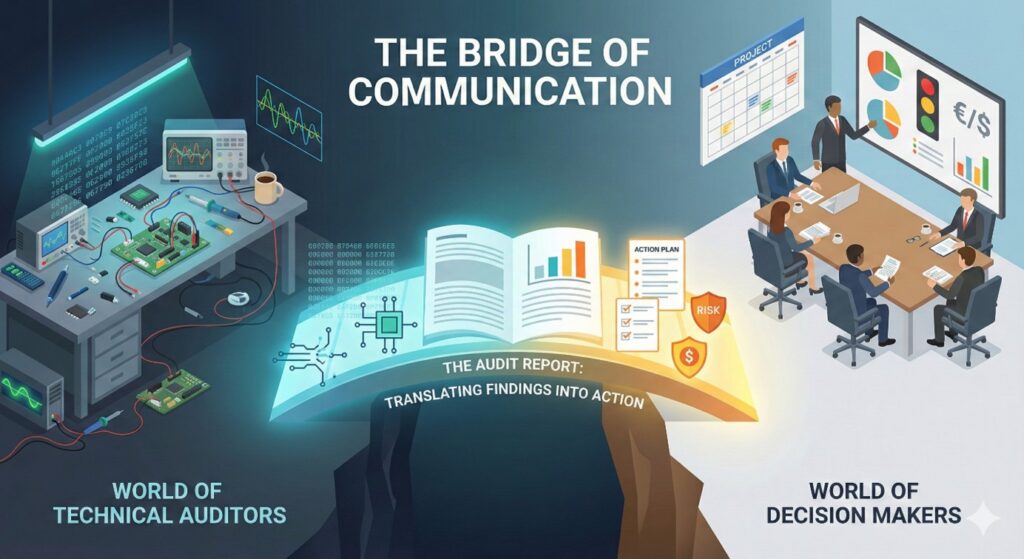
Finally, all this work culminates in the writing of a report. This document summarizes the findings, details the methods used, and provides concrete recommendations for improving security. Often, this report is what makes the difference for the product team, as it enables them to move from awareness to action.
Why every step matters (and why they're so demanding)
Each of these steps comes with its own set of challenges. Reconnaissance involves navigating through incomplete sources of information and/or poorly documented components. Disassembly requires precision, one wrong move and the board could be damaged. Technical analysis demands a delicate balance of skills in electronics, computer science, and cybersecurity. As for exploiting discovered vulnerabilities, it tests the pentester’s ingenuity, often requiring improvisation when facing systems specifically designed to resist curiosity. Finally, writing the report requires a pedagogical approach to make an often highly technical subject accessible.
This is where many auditors face reality: without the right tools, hardware auditing can quickly turn into a time-consuming, error-prone headache.. The diversity of protocols, the complexity of components, and the lack of standardization make the task challenging, even for the most experienced pentesters
Hardsploit NG: the game-changing companion
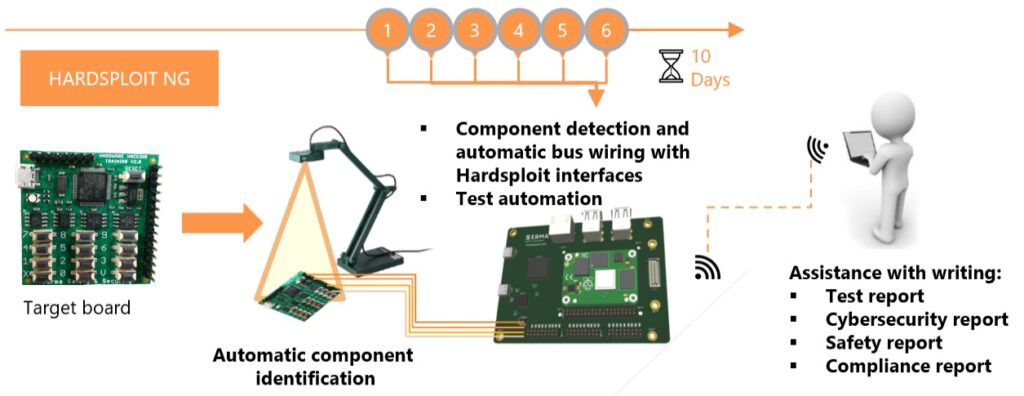
In the face of these challenges, Hardsploit NG aims to be a true ally for auditors and pentesters, whether experienced or not. Designed as a Swiss army knife for hardware pentesting, it supports the auditor throughout every stage of the process.
From the component identification phase, automated AI recognition helps identify components and find relevant documentation. During the analysis phase, the tool automates many tedious tasks: interface detection, associated communication protocols, firmware extraction methods, etc. This allows the auditor to focus on what truly matters, understanding the system’s behavior and spotting vulnerabilities.
When it comes to exploitation, Hardsploit NG enables the creation of tailored scripts for each type of attack, whether it’s reading memory, injecting commands, or manipulating protocols. Finally, automated report generation is built into the platform. The results are presented clearly, with concrete recommendations ready to be passed on to the development or security teams.
This global approach saves time, reduces errors and makes hardware auditing accessible to a much wider audience than before
What’s coming next
This post is only the introduction to the journey into the world of hardware penetration testing. In the upcoming blog posts, we’ll take a closer look at each of the steps mentioned above. You’ll discover how Hardsploit NG makes the auditor’s job easier, from the very first interaction with the device, through technical analysis and vulnerability exploitation, all the way to the final report.
So, are you ready to follow the red thread of hardware pentesting? Stay tuned, more is coming very soon!
Protect your equipment with Hardsploit NG, our cutting‑edge hardware and IoT auditing solution.