Blog post 2 #5
Chaque campagne d’audit matériel se conclut par une étape cruciale souvent sous-estimée : la restitution des résultats.
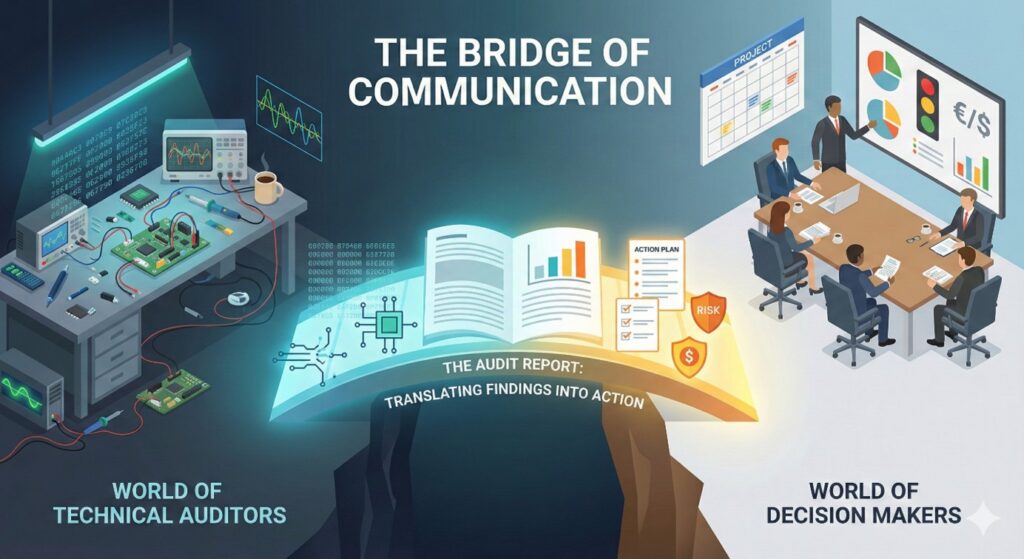
Every hardware security audit campaign ends with a critical step that is often underestimated: the restitution of results. After days—or sometimes weeks—of investigation, analysis, and exploitation, the challenge is to clearly communicate what has been discovered, assessed, and understood.
An audit report is not just an administrative deliverable. It acts as a bridge between the technical world of auditors and decision-makers, developers, security managers, and project leads. When properly structured, it turns investigative work into a clear and actionable plan to strengthen a product’s security posture.
The report: A communication tool, not just a technical record
A good audit report must meet two essential requirements: rigor and clarity. It is intended for multiple audiences with very different expectations.
The executive summary presents the key findings to a non-technical readership. It outlines the audit context, the major risks identified, the overall security level, and—most importantly—the prioritization of remediation actions. The objective is to provide a clear vision: Is immediate action required, and where should efforts be focused?
The methodology and scope describe the approach taken, the tools used, any limitations encountered, and the areas or functionalities that were excluded from the assessment. This section ensures transparency and traceability throughout the audit process.
Finally, the detailed findings form the technical core of the report. They include vulnerability exploitation details, severity levels (often using a CVSS score adapted to embedded systems), functional and business impacts, reproducible proofs of concept (PoCs), and specific remediation recommendations. Each vulnerability is documented with a high level of detail, enabling engineering teams to reproduce, understand, and effectively fix the issue.
Adapting the message to support decision-making
A well-designed audit report does not attempt to say everything—it says what matters, in a clear and actionable way. The level of technical detail must be carefully adjusted. Flooding an executive committee with logs and memory addresses is pointless, just as providing vague assessments to a development team is ineffective.
The auditor’s role is therefore also that of an educator. The goal is to convey the stakes without distorting the technical reality, and to propose concrete, testable, and realistic remediation measures—especially when dealing with hardware, where changes are often more costly or risky than software fixes.
Ultimately, a successful audit report becomes a decision-support tool. It allows an organization to assess its risks, plan corrective actions, and track remediation progress. Without this formalization step, even the most thorough analysis loses its impact: a vulnerability that is discovered but poorly explained remains… an unpatched vulnerability.

Hardsploit NG: automating to communicate more effectively
One of the major innovations of Hardsploit NG will be its ability to automatically generate audit reports. By systematically recording interactions between the tool and the target device, every operation—register reads, bus captures, or hardware manipulations—can be archived, contextualized, and directly integrated into a preformatted report.
This automation will significantly reduce the time spent documenting results and eliminate the risk of missing critical steps. Proofs of concept, captures, logs, and metadata will be grouped in a structured and coherent manner.
Auditors will be able to focus on analysis and the formulation of meaningful recommendations rather than on report formatting. For the teams receiving the report, this complete traceability will ensure reproducibility of findings and full transparency of the audit process. In short, Hardsploit NG will not only assist auditors during the analysis phases; it will also simplify the valorization of their work by generating documented, understandable, and immediately actionable deliverables.

Closing the loop
Throughout this article series, each step of a hardware penetration test has highlighted the complexity and rigor required to produce a reliable embedded security assessment. From opening the enclosure to analyzing internal components, from exploiting vulnerabilities to writing the final report, the auditor navigates between investigation, engineering, and pedagogy, relying on a proven methodology.
In this context, Hardsploit NG aims to become a key ally for auditors and penetration testers. With automated action logging, reproducible report generation, and integration with open-source analysis tools, it promises to simplify reporting and strengthen the reliability of results communication. With this new generation of tools in development, the pentester will no longer be merely a vulnerability discoverer, but a central actor in the continuous improvement cycle of hardware security—supported by a robust and innovative platform designed to meet the complex challenges of modern electronic systems.